possession factor
What is a possession factor?
The possession factor, in a security context, is a category of user authentication credentials based on items that the user has with them, typically a hardware device such as a security token or a mobile phone used in conjunction with a software token.
Mandating the use of a possession factor is a common approach in security systems based on two-factor authentication (2FA) and multifactor authentication (MFA). Typically, 2FA and MFA systems also require users to provide a knowledge factor such as a password, PIN, or answer to a secret question and/or an inherence factor such as a fingerprint, faceprint or voice sample.
What is 2FA and MFA?
2FA is an authentication approach in security in which authorized users are required to provide two factors to access a system or account. Both factors are required for the user to confirm their identity and prove to the system that they are allowed access and use. The required authentication factors might be some combination of knowledge, inherence, and possession factors.
2FA provides greater security than single-factor authentication (SFA) systems that are username- or password-based. This is because it's harder for a threat actor to get both factors in order to compromise or damage an account or the data residing within it. For this reason, many organizations prefer 2FA over SFA to protect their business-critical assets and sensitive data.
MFA is like 2FA and has similar security goals. The only difference is that MFA requires the use of two or more authentication factors whereas 2FA requires the use of only two factors.
MFA is becoming increasingly common for mobile authentication, two-factor authentication in particular. Google Authenticator, for example, requires the user to log in to websites as usual and then input a time-based one-time password that is sent to the registered device.
What are the authentication factors in 2FA and MFA?
There are three main categories of user authentication factors used in 2FA and MFA systems:
- Possession factor: something the user has, such as a mobile phone or USB dongle.
- Knowledge factor: something the user knows, such as a PIN or password.
- Inherence factor: something the user is, typically a biological characteristic captured as biometric data, such as fingerprints or voiceprints.
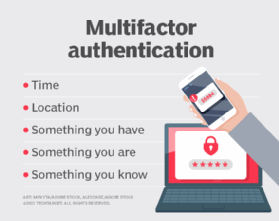
2FA uses elements from two of the three categories; three-factor authentication (3FA) involves elements from each of the main categories. Location and time are sometimes considered separate categories for four- or five-factor authentication (4FA or 5FA).
What is the possession factor in MFA and 2FA?
Devices like security tokens and mobile phones represent the possession factor in 2FA and MFA. A possession factor simply refers to a physical item possessed by a user that allows him or her to access an online tool or account. Access to the account is restricted to specific users and having the possession factor ensures that those users are part of the allowed list.
Here are some examples of the most common possession factors used today for authentication:
- Mobile phones that receive a PIN.
- Hardware tokens like electronic keycards, key fobs and USB dongles that generate a one-time password (OTP).
- Smart card with an embedded integrated circuit chip; typically used to secure sensitive transactions and systems, such as financial, healthcare and educational systems.
- FIDO2 (Fast Identity Online) security key that facilitates USB, Bluetooth or NFC-based access without the need for a password (that can be guessed or stolen).

Benefits of using a possession factor
Traditional authentication systems are of the SFA type. SFA systems, such as the familiar user name and password combination, are increasingly considered inadequate in the context of cybersecurity and information security.
One reason is that usernames are easily guessed; another is password cracking. Adding the possession element to logins for two-factor authentication significantly increases the security of the system or account because the users must know their passwords and possess the registered devices associated with their accounts.
When a user tries to access an account using the possession factor, the system checks the validity of that piece of hardware before allowing access. Security keys based on the FIDO2 standard are among the strongest and most reliable possession factors available today. Many keys are based on biometric authentication, meaning they combine the possession factor with the inherence factor to further strengthen account security and prevent unauthorized, i.e., malicious users from accessing the account.
Threat actors trying to compromise the account would have to get past two authentication factors, which is difficult to do. For example, they would not only have to steal the user's username or password, but also gain physical access to the key to fool the system and gain access.
Authentication possession factor risks
Adding a possession factor strengthens the security of a system. That said, the possession factor doesn't ensure 100% security because it is based on physical possession, meaning the authorized user must physically possess the smartcard, security key or hardware token to access an account. Keeping the device in a safe place can prevent hackers from using it for malicious purposes. However, if the authorized user is careless, a threat actor might be able to steal the device and use it to access the account the device is meant to protect.
The threat actor might also use social engineering techniques to convince the authorized user to give them access to the device. Increasingly, threat actors eavesdrop on the communications between the authorized user and the security system -- an approach known as man-in-the-middle attacks -- in order to steal the authorized user's identity and access their account.
Despite these risks, adding a possession factor to an authentication system provides much stronger security than knowledge factors like usernames and passwords. Possession factors and MFA are also key components of zero-trust architecture, a security model in which no user or device is implicitly trusted, which ensures more robust security than traditional perimeter security.
Discover five strategies to mitigate vulnerabilities in MFA. Further explore five common authentication factors. Check out four essential identity and access management best practices and see how to fix the top five cybersecurity vulnerabilities.







