information rights management (IRM)
What is information rights management?
Information rights management (IRM) is a discipline that involves managing, controlling and securing content from unwanted access. IRM is a subset of digital rights management (DRM), which protects multimedia content, including video and music.
DRM technology protects intellectual property and sensitive information from patent and copyright infringement and piracy. By contrast, IRM protects sensitive data, especially data that's exchanged with parties outside an organization, such as suppliers and partners.
With increases in cybersecurity attacks and other unauthorized access events, information of all kinds must be actively protected. Effective data security and protection strategies prevent business disruptions, financial losses, destruction of business-critical data and damage to an organization's reputation.
How does IRM work?
IRM is part of broader digital asset management (DAM) systems and processes, which organize, store and retrieve rich media digital content.
In practice, rights management services use encryption to protect sensitive documents and confidential information resources from unauthorized user access. IRM rules might permit viewing but prohibit copying and pasting of the content elsewhere or taking screenshots. IRM typically translates into specific rules that govern how documents can be accessed and used.
When a user requests access to a restricted document, authentication is required. The request goes to a special server that reviews a list of approved viewers; if the credentials match, the system issues a release license for access. The system might specify specific permissions, such as read-only or no copying. IRM apps create additional IT overhead with the associated costs that must be evaluated against perceived security threats.
IRM has some limitations. Implementing it often requires the use of specialized applications that encapsulate the content. IRM protection can be bypassed in several ways, such as hand-copying or retyping content, using screen capture features and by taking a photo of a document.
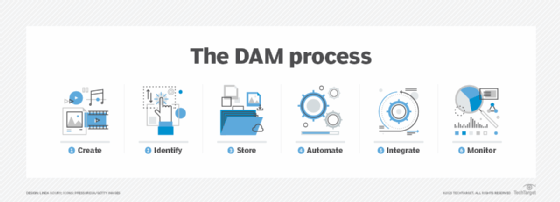
Components of an IRM strategy
An IRM strategy, along with related policies and procedures, address several data protection issues and provide a range of functionality, such as the following:
- Defining file use and file sharing attributes.
- Setting parameters for remotely accessing content.
- Defining access controls for documents and other content.
- Identifying how documents are tracked.
- Specifying how encryption is used.
- Defining who has access.
Many productivity platforms, such as Microsoft Office 365 and Outlook, have embedded IRM features.
Why is IRM important?
There are several reasons IRM is an important consideration, including the following:
- Document types. IRM is critical to all sorts of enterprise document files, including Word documents, Excel spreadsheets and PowerPoint presentations.
- Security. It's a key part of a data protection strategy, protecting files from unauthorized actions, such as viewing, copying, printing, forwarding, deleting or editing.
- Compliance. IRM helps organizations comply with data protection and security standards and regulations. For example, the European Union's General Data Protection Regulation requires significant data protection capabilities.
- Audits. The ability to demonstrate information and data protection controls is an important IT audit consideration. Demonstrating an IRM policy with associated procedures and systems to implement IRM is important audit evidence.
- Broad protection. IRM-protected documents retain their protection regardless of where the files are located and or how they're accessed.
Who uses IRM?
The need to protect certain kinds of information, such as document files and customer records, from unauthorized access can justify the need for IRM technology. Any organization that has a data protection policy can benefit by using IRM.
For example, in healthcare, the Health Insurance Portability and Accountability Act requires the protection of electronic patient health information. IRM is combined with other document security practices to ensure patient data is protected.
Find out more about how digital asset management works and is used.







